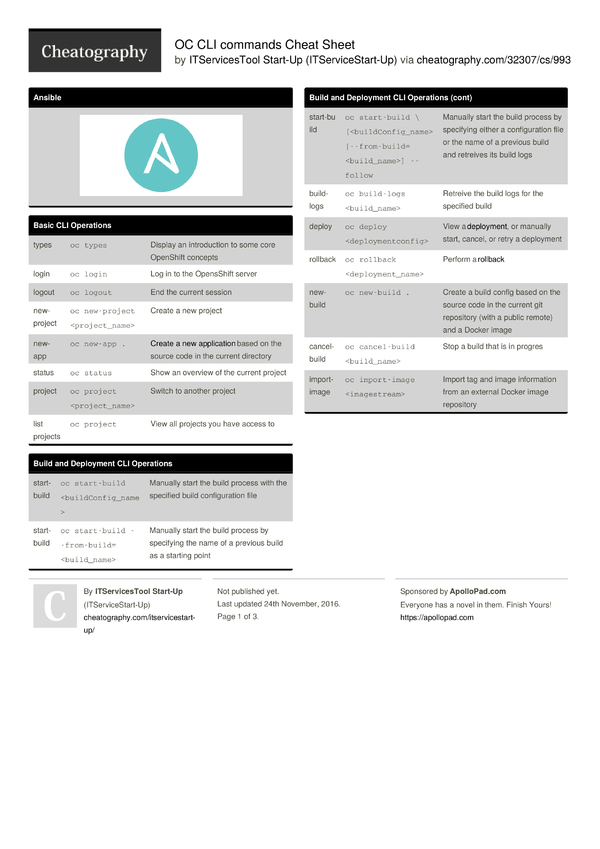
In today's digital age, IoTSH login CLI commands have become essential for managing and securing IoT devices. As the Internet of Things continues to expand, understanding these commands is crucial for professionals and enthusiasts alike. Whether you're a network administrator or a tech enthusiast, mastering IoTSH CLI commands will empower you to manage your devices more effectively.
As the world becomes increasingly interconnected, the need for robust command-line tools has grown exponentially. IoTSH login CLI commands provide a powerful way to interact with IoT devices, ensuring they remain secure and functional. These commands are designed to simplify complex tasks, offering users greater control over their devices.
This guide will walk you through everything you need to know about IoTSH login CLI commands, from basic operations to advanced techniques. By the end of this article, you'll have a solid understanding of how to use these commands to enhance your IoT management capabilities.
Read also:What Is Evooli And Why Should You Care About It
Table of Contents
- Introduction to IoTSH Login CLI Commands
- Basic IoTSH CLI Commands
- Advanced IoTSH CLI Commands
- Security Best Practices for IoTSH CLI
- Troubleshooting IoTSH CLI Issues
- Real-World Use Cases of IoTSH CLI
- Comparison with Other CLI Tools
- Tips for Efficient IoTSH CLI Usage
- Future Trends in IoTSH CLI Technology
- Conclusion and Next Steps
Introduction to IoTSH Login CLI Commands
The Internet of Things (IoT) has revolutionized the way we interact with technology. IoTSH login CLI commands are an integral part of this ecosystem, providing users with the tools needed to manage and secure their devices effectively. These commands allow for seamless interaction with IoT devices, enabling users to perform tasks such as device configuration, monitoring, and troubleshooting.
Understanding IoTSH login CLI commands is essential for anyone working in the IoT field. Whether you're configuring a smart home device or managing an entire network of IoT sensors, these commands offer the precision and control needed to ensure optimal performance. By familiarizing yourself with these tools, you can streamline your workflow and improve your overall efficiency.
Basic IoTSH CLI Commands
Logging In to IoTSH
Before you can start managing your IoT devices, you need to log in to the IoTSH platform. The basic login command is straightforward:
iotsh login --username [your_username] --password [your_password]
This command prompts the system to authenticate your credentials and grant access to the IoTSH environment. Once logged in, you can begin exploring the various functionalities available through the CLI interface.
Read also:What Is Secure Shell In Iot And How It Works
Device Management
Managing devices is one of the primary functions of IoTSH CLI commands. Here are some basic commands for device management:
iotsh devices list: Displays a list of all connected devices.iotsh device info [device_id]: Retrieves detailed information about a specific device.iotsh device status [device_id]: Checks the current status of a device.
These commands provide a foundation for interacting with your IoT devices, allowing you to monitor and manage them with ease.
Advanced IoTSH CLI Commands
Configuration Settings
Advanced users often require more granular control over their IoT devices. IoTSH CLI commands offer several options for configuring device settings:
iotsh config set [parameter] [value]: Sets a specific configuration parameter for a device.iotsh config get [parameter]: Retrieves the current value of a configuration parameter.iotsh config reset [device_id]: Resets a device's configuration to its default settings.
These commands enable users to fine-tune their devices, ensuring they operate according to specific requirements.
Script Automation
For repetitive tasks, script automation can save time and reduce errors. IoTSH CLI supports scripting through batch commands:
iotsh batch --file [script_file]
This command executes a series of predefined instructions stored in a script file, streamlining complex operations and improving efficiency.
Security Best Practices for IoTSH CLI
Security is a top priority when working with IoT devices. IoTSH login CLI commands include several features designed to enhance security:
- Two-factor authentication (2FA) for login processes.
- Encrypted communication protocols to protect data in transit.
- Role-based access control (RBAC) to restrict unauthorized access.
Implementing these best practices ensures your IoT devices remain secure and protected from potential threats.
Troubleshooting IoTSH CLI Issues
Common Errors
Even experienced users may encounter issues when using IoTSH CLI commands. Here are some common errors and their solutions:
- Error: Authentication failed: Verify your username and password. Ensure two-factor authentication is enabled if required.
- Error: Device not found: Check the device ID and ensure it is correctly registered in the IoTSH platform.
- Error: Command not recognized: Confirm the syntax of your command and ensure you are using the latest version of the CLI tool.
Debugging Tools
IoTSH CLI includes built-in debugging tools to help diagnose and resolve issues:
iotsh debug start: Initiates a debugging session to capture detailed logs.iotsh debug stop: Terminates the debugging session and saves the logs for analysis.
These tools provide valuable insights into system behavior, helping users identify and resolve problems more effectively.
Real-World Use Cases of IoTSH CLI
IoTSH login CLI commands have a wide range of applications across various industries. Here are some real-world use cases:
- Smart Home Automation: Manage and monitor smart home devices, such as thermostats, lighting systems, and security cameras.
- Industrial IoT: Monitor and control industrial equipment, ensuring optimal performance and minimizing downtime.
- Healthcare: Manage medical devices and sensors, enabling remote patient monitoring and improving healthcare outcomes.
These use cases demonstrate the versatility and power of IoTSH CLI commands in transforming how we interact with technology.
Comparison with Other CLI Tools
While IoTSH CLI commands offer a robust set of features, it's important to compare them with other CLI tools in the market:
- Advantages: IoTSH CLI provides a user-friendly interface, extensive documentation, and strong security features.
- Disadvantages: Some users may find the learning curve steep, especially for advanced functionalities.
By evaluating these factors, users can determine whether IoTSH CLI is the right tool for their needs.
Tips for Efficient IoTSH CLI Usage
To get the most out of IoTSH CLI commands, consider the following tips:
- Regularly update your CLI tool to ensure you have access to the latest features and security patches.
- Document your commands and scripts for future reference, saving time and reducing errors.
- Participate in online communities and forums to learn from other users and stay informed about best practices.
These tips will help you become more proficient in using IoTSH CLI commands, enhancing your overall experience.
Future Trends in IoTSH CLI Technology
As technology continues to evolve, so too will IoTSH CLI commands. Some emerging trends include:
- Artificial Intelligence Integration: AI-powered CLI tools that predict user needs and automate routine tasks.
- Enhanced Security Features: Advanced encryption and authentication methods to protect sensitive data.
- Cloud-Based Solutions: Greater reliance on cloud platforms to manage and store IoT device data.
Staying informed about these trends will ensure you remain at the forefront of IoT technology.
Conclusion and Next Steps
In conclusion, mastering IoTSH login CLI commands is essential for anyone working with IoT devices. From basic operations to advanced techniques, these commands offer unparalleled control and flexibility. By following the tips and best practices outlined in this guide, you can enhance your IoT management capabilities and stay ahead of the curve.
We invite you to share your thoughts and experiences in the comments section below. Your feedback helps us improve and create more valuable content. Additionally, explore our other articles for more insights into the world of IoT and technology.