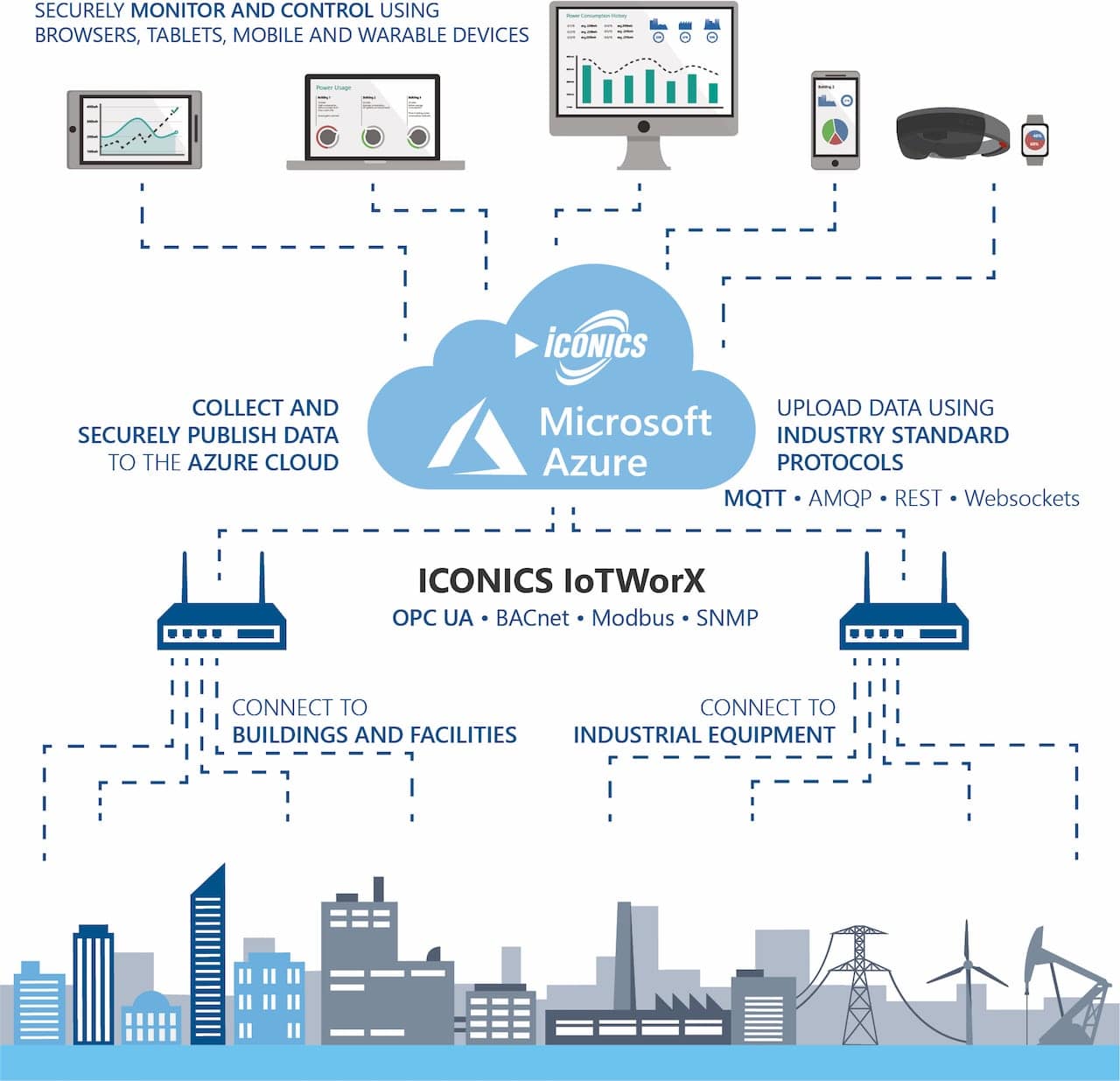
Connecting remote IoT devices securely through P2Psh on Windows 10 is a crucial step in ensuring your network remains protected while maintaining seamless communication between devices. The increasing reliance on Internet of Things (IoT) devices has transformed the way we interact with technology. Whether for personal or professional use, IoT devices offer unparalleled convenience. However, as these devices become more integrated into our daily lives, the importance of secure connections cannot be overstated.
As you explore the possibilities of remote IoT connections, it is essential to understand the risks associated with unsecured networks. A secure connection not only protects your data but also ensures that your devices function optimally without unauthorized interference. By leveraging P2Psh technology on Windows 10, you can create a robust and secure environment for your IoT ecosystem.
This guide will walk you through the process of securely connecting remote IoT devices using P2Psh on Windows 10. We'll cover everything from setting up your environment to troubleshooting common issues. Whether you're a beginner or an experienced user, this article will provide valuable insights to help you achieve a secure and efficient IoT setup.
Read also:Andrea Bocelli The Timeless Voice Of Passion And Inspiration
Table of Contents
- Introduction to Secure IoT Connections
- What is P2Psh and Why Use It?
- Setting Up Windows 10 for IoT
- Implementing Security Measures
- Connecting IoT Devices
- Troubleshooting Common Issues
- Best Practices for Secure Connections
- Data Protection Strategies
- Optimizing Performance
- Conclusion and Call to Action
Introduction to Secure IoT Connections
Why Security Matters in IoT
In today's interconnected world, IoT devices have become an integral part of our daily lives. From smart home appliances to industrial automation systems, IoT offers countless benefits. However, the security of these devices is often overlooked, leaving them vulnerable to cyber threats. A secure connection is vital to protect sensitive data and maintain the integrity of your IoT network.
Connecting remote IoT devices securely requires a combination of robust protocols, encryption methods, and reliable software. By leveraging P2Psh technology, you can create a secure channel for communication between devices, ensuring that your data remains protected from unauthorized access.
Windows 10 provides a powerful platform for managing IoT devices, offering built-in security features and compatibility with various third-party tools. Understanding how to configure and secure your IoT setup on Windows 10 is essential for maintaining a safe and efficient network.
What is P2Psh and Why Use It?
Understanding Peer-to-Peer Technology
P2Psh is a peer-to-peer (P2P) technology designed to facilitate secure and efficient communication between devices. Unlike traditional client-server models, P2Psh allows devices to communicate directly without the need for a centralized server. This reduces latency, improves performance, and enhances security by minimizing potential points of failure.
Using P2Psh for IoT connections offers several advantages:
- Enhanced Security: Direct communication between devices reduces the risk of data breaches.
- Improved Efficiency: P2Psh eliminates the need for intermediaries, resulting in faster and more reliable connections.
- Scalability: P2P networks can easily accommodate a growing number of devices without compromising performance.
By incorporating P2Psh into your IoT setup, you can create a secure and resilient network capable of handling complex tasks and large volumes of data.
Read also:Discover The Best Del Webb California Locations For Your Dream Retirement
Setting Up Windows 10 for IoT
Preparing Your Environment
Before you can securely connect remote IoT devices using P2Psh on Windows 10, you need to ensure your system is properly configured. Start by updating your operating system to the latest version to take advantage of the latest security features and improvements.
Here are some key steps to prepare your Windows 10 environment:
- Install the latest updates and security patches.
- Enable Windows Defender Firewall and configure it to allow P2Psh traffic.
- Install any required drivers and software for your IoT devices.
Once your system is ready, you can proceed to configure P2Psh settings to establish secure connections with your IoT devices.
Implementing Security Measures
Protecting Your IoT Network
Securing your IoT network is critical to protecting sensitive data and maintaining the integrity of your devices. Implementing robust security measures is essential to prevent unauthorized access and potential cyberattacks.
Consider the following security measures:
- Use Strong Passwords: Ensure all devices and accounts have unique and complex passwords.
- Enable Encryption: Use end-to-end encryption to secure data transmitted between devices.
- Regularly Update Firmware: Keep your IoT devices up to date with the latest firmware to address security vulnerabilities.
By combining these measures with P2Psh technology, you can create a secure and reliable IoT network that protects your data and devices from potential threats.
Connecting IoT Devices
Establishing Secure Connections
Connecting IoT devices securely using P2Psh on Windows 10 involves several steps. Start by identifying the devices you wish to connect and ensuring they are compatible with P2Psh technology. Next, configure the necessary settings on both your Windows 10 system and the IoT devices.
Follow these steps to establish secure connections:
- Install the P2Psh client software on your Windows 10 system.
- Configure the P2Psh settings to match your network requirements.
- Pair your IoT devices with the P2Psh network using the provided instructions.
Once the connections are established, test the communication between devices to ensure everything is functioning as expected.
Troubleshooting Common Issues
Resolving Connection Problems
While setting up secure IoT connections using P2Psh on Windows 10, you may encounter various issues. Understanding how to troubleshoot these problems is essential for maintaining a stable and secure network.
Some common issues and their solutions include:
- Connection Failures: Check network settings and ensure all devices are properly configured.
- Performance Issues: Optimize P2Psh settings and update firmware to improve performance.
- Security Alerts: Review firewall and encryption settings to address any security concerns.
By addressing these issues promptly, you can ensure your IoT network remains secure and functional.
Best Practices for Secure Connections
Maintaining a Secure IoT Environment
Adopting best practices for secure IoT connections is crucial for long-term success. Regularly reviewing and updating your security measures will help protect your network from emerging threats.
Here are some best practices to follow:
- Conduct regular security audits to identify and address vulnerabilities.
- Limit access to your IoT network to authorized users only.
- Monitor network activity for any suspicious behavior and respond promptly.
By adhering to these practices, you can maintain a secure and efficient IoT network that meets your needs.
Data Protection Strategies
Securing Sensitive Information
Protecting sensitive data is a top priority when managing IoT devices. Implementing effective data protection strategies ensures that your information remains secure and confidential.
Consider the following strategies:
- Data Encryption: Use strong encryption methods to secure data at rest and in transit.
- Access Controls: Implement role-based access controls to restrict data access to authorized personnel.
- Backup Solutions: Regularly back up important data to prevent loss in case of a security breach.
By incorporating these strategies into your IoT setup, you can safeguard your data and maintain the trust of your users.
Optimizing Performance
Improving Network Efficiency
Optimizing the performance of your IoT network is essential for ensuring seamless communication between devices. By fine-tuning your P2Psh settings and implementing best practices, you can achieve maximum efficiency and reliability.
Here are some tips for optimizing performance:
- Adjust P2Psh settings to match your network's specific requirements.
- Monitor network performance regularly and make adjustments as needed.
- Upgrade hardware and software components to improve overall performance.
By focusing on performance optimization, you can create a robust and efficient IoT network that meets the demands of modern applications.
Conclusion and Call to Action
Securing remote IoT connections using P2Psh on Windows 10 is a critical step in protecting your network and ensuring seamless communication between devices. By following the guidelines outlined in this article, you can create a secure and efficient IoT setup that meets your needs.
Remember to implement robust security measures, adopt best practices, and regularly update your system to address emerging threats. Your feedback is valuable to us, so please feel free to leave a comment or share this article with others who may benefit from it. Additionally, explore our other resources for more information on IoT security and optimization.
Stay informed, stay secure, and take control of your IoT network today!