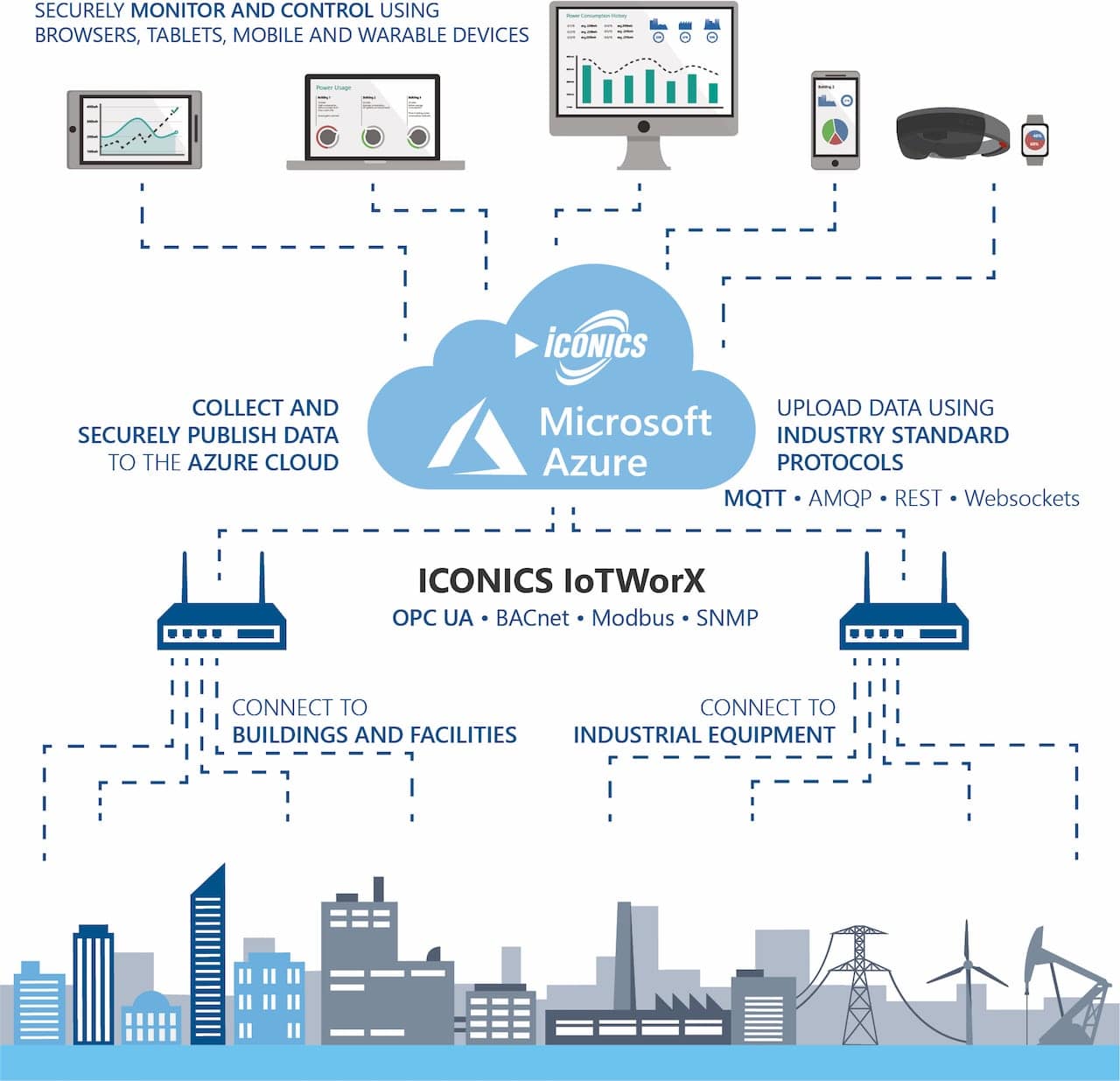
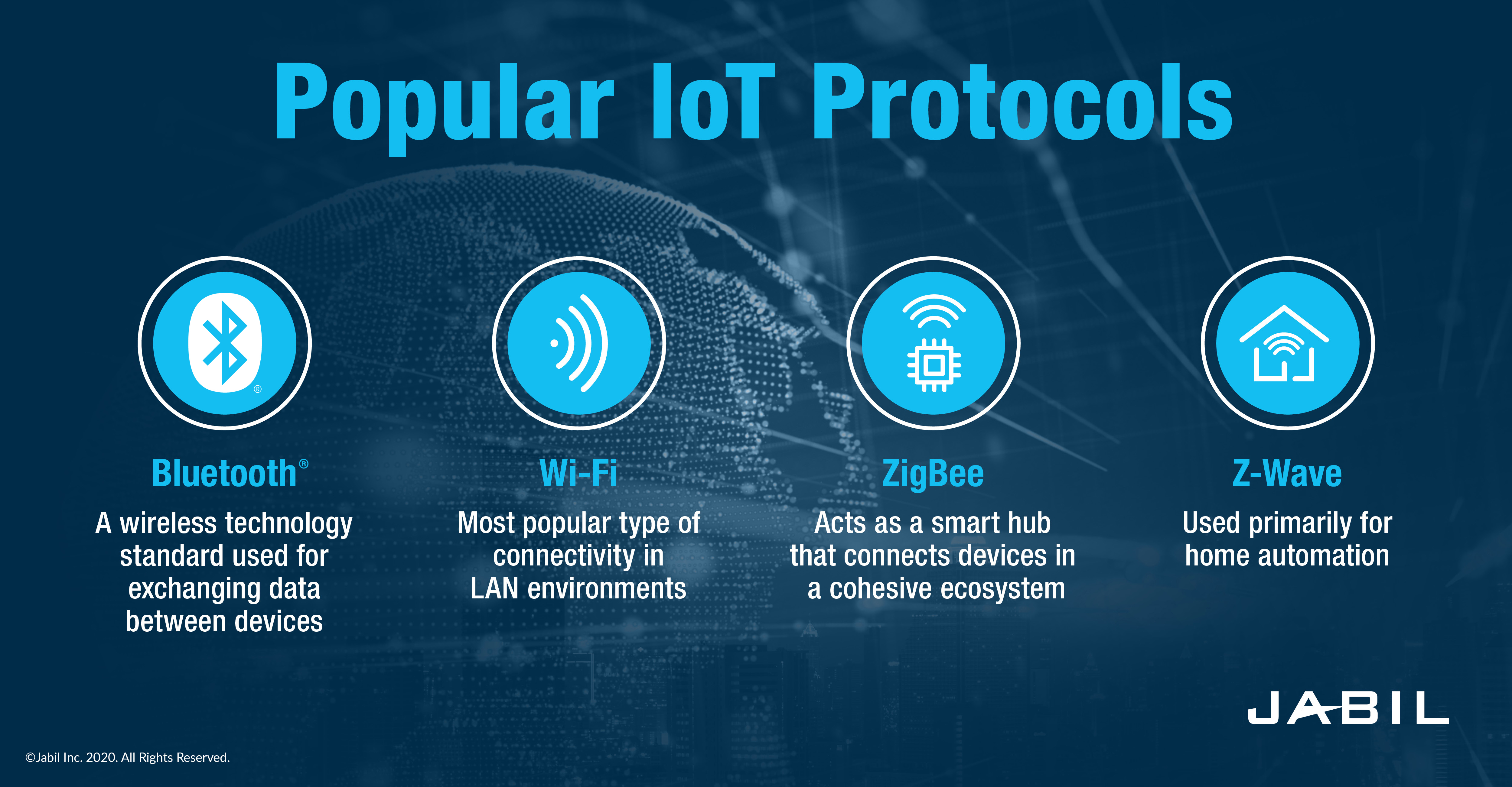
In today's interconnected world, securely connecting remote IoT devices for peer-to-peer (P2P) download is a crucial aspect of modern technology. The rise of IoT devices has transformed how businesses and individuals interact with technology, creating both opportunities and challenges. Ensuring secure connections is not just a technical necessity but also a fundamental requirement for safeguarding sensitive data.
As the Internet of Things (IoT) continues to expand, the need for secure communication between devices becomes increasingly important. This guide aims to provide you with actionable insights and strategies to establish robust connections while mitigating potential risks associated with remote IoT P2P downloads.
By the end of this article, you will gain a deeper understanding of the technical aspects, security measures, and best practices involved in securely connecting IoT devices for peer-to-peer downloads. Whether you are a tech enthusiast, a developer, or a business owner, this guide will equip you with the knowledge to navigate this complex landscape effectively.
Read also:Everything You Need To Know About 4 Movierulz 2025 Download
Table of Contents
- Introduction to IoT
- Importance of Security in IoT
- Overview of P2P Download
- Securely Connect Remote IoT P2P Download
- Challenges in IoT Security
- Best Practices for IoT Security
- Encryption Techniques for IoT
- Data Protection in IoT
- Future Trends in IoT Security
- Conclusion
Introduction to IoT
The Internet of Things (IoT) refers to the network of interconnected devices that communicate and exchange data over the internet. These devices range from smart home appliances to industrial sensors, all designed to enhance efficiency, convenience, and automation.
IoT devices rely on various communication protocols and technologies to function effectively. Understanding the basics of IoT is essential for grasping the complexities of securely connecting remote IoT devices for peer-to-peer downloads.
Key Components of IoT
- Sensors: Devices that collect data from the environment.
- Gateways: Intermediate devices that facilitate communication between sensors and the cloud.
- Cloud Platforms: Centralized systems that store and process IoT data.
Importance of Security in IoT
Security is a critical concern in the realm of IoT, especially when it comes to remotely connecting devices for peer-to-peer downloads. With the increasing number of connected devices, the risk of cyberattacks and data breaches also grows.
Securing IoT devices involves implementing robust authentication, encryption, and monitoring mechanisms to protect sensitive information and maintain system integrity.
Risks Associated with IoT Security
- Data breaches
- Unauthorized access
- Malware attacks
Overview of P2P Download
Peer-to-peer (P2P) downloading is a method of file sharing where devices directly exchange data without relying on a central server. This approach offers several advantages, including reduced bandwidth consumption and improved download speeds.
However, P2P downloading also introduces unique security challenges, particularly when applied to IoT devices. Ensuring secure connections is paramount to prevent unauthorized access and data leakage.
Read also:What Did Shawn Dawson Do Unraveling His Journey And Impact
Benefits of P2P Download
- Efficient resource utilization
- Decentralized architecture
- Scalability
Securely Connect Remote IoT P2P Download
Establishing secure connections for remote IoT P2P downloads requires a multi-layered approach. This involves implementing encryption, authentication, and monitoring protocols to safeguard data and ensure device integrity.
Here are some key strategies for securely connecting IoT devices:
Authentication Protocols
- Use strong passwords and multi-factor authentication (MFA).
- Implement device-specific certificates for secure identification.
Encryption Techniques
- Utilize AES-256 encryption for secure data transmission.
- Employ TLS/SSL protocols to protect communication channels.
Challenges in IoT Security
Despite advancements in technology, securing IoT devices for remote P2P downloads remains a challenging task. Some of the primary challenges include:
- Limited computational resources on IoT devices.
- Fragmented standards and protocols.
- Difficulty in updating firmware on deployed devices.
Best Practices for IoT Security
To enhance the security of IoT devices during remote P2P downloads, consider the following best practices:
- Regularly update firmware and software.
- Implement network segmentation to isolate critical devices.
- Monitor network activity for suspicious behavior.
Security Audits
Conducting periodic security audits is essential for identifying vulnerabilities and addressing them proactively. This involves reviewing system configurations, testing encryption protocols, and assessing access controls.
Encryption Techniques for IoT
Encryption plays a vital role in securing IoT devices during remote P2P downloads. Advanced encryption standards (AES) and transport layer security (TLS) are commonly used to protect data in transit.
For resource-constrained IoT devices, lightweight encryption algorithms such as Elliptic Curve Cryptography (ECC) are preferred due to their efficiency and security.
Data Protection in IoT
Data protection is a critical aspect of IoT security, especially when dealing with sensitive information. Implementing data protection measures involves encrypting data at rest and in transit, as well as enforcing strict access controls.
Compliance with regulations such as GDPR and HIPAA ensures that organizations adhere to best practices for data protection.
Future Trends in IoT Security
The future of IoT security is shaped by emerging technologies and evolving standards. Some of the key trends to watch include:
- Blockchain for secure and decentralized communication.
- AI-driven threat detection and response systems.
- Quantum encryption for ultra-secure data transmission.
Impact of Emerging Technologies
Emerging technologies such as 5G and edge computing are expected to revolutionize IoT security by enabling faster and more secure communication. These advancements will pave the way for innovative solutions that address current security challenges.
Conclusion
Securing remote IoT devices for P2P downloads is a complex yet essential task in today's digital landscape. By implementing robust security measures, organizations can protect sensitive data and maintain system integrity.
We encourage you to explore the topics discussed in this guide and apply the best practices outlined to enhance your IoT security strategy. Feel free to share your thoughts in the comments section and explore other articles on our website for more insights into technology and security.
Sources:
- https://www.nist.gov
- https://www.cisco.com
- https://www.iso.org